Unified Application
Security Platform
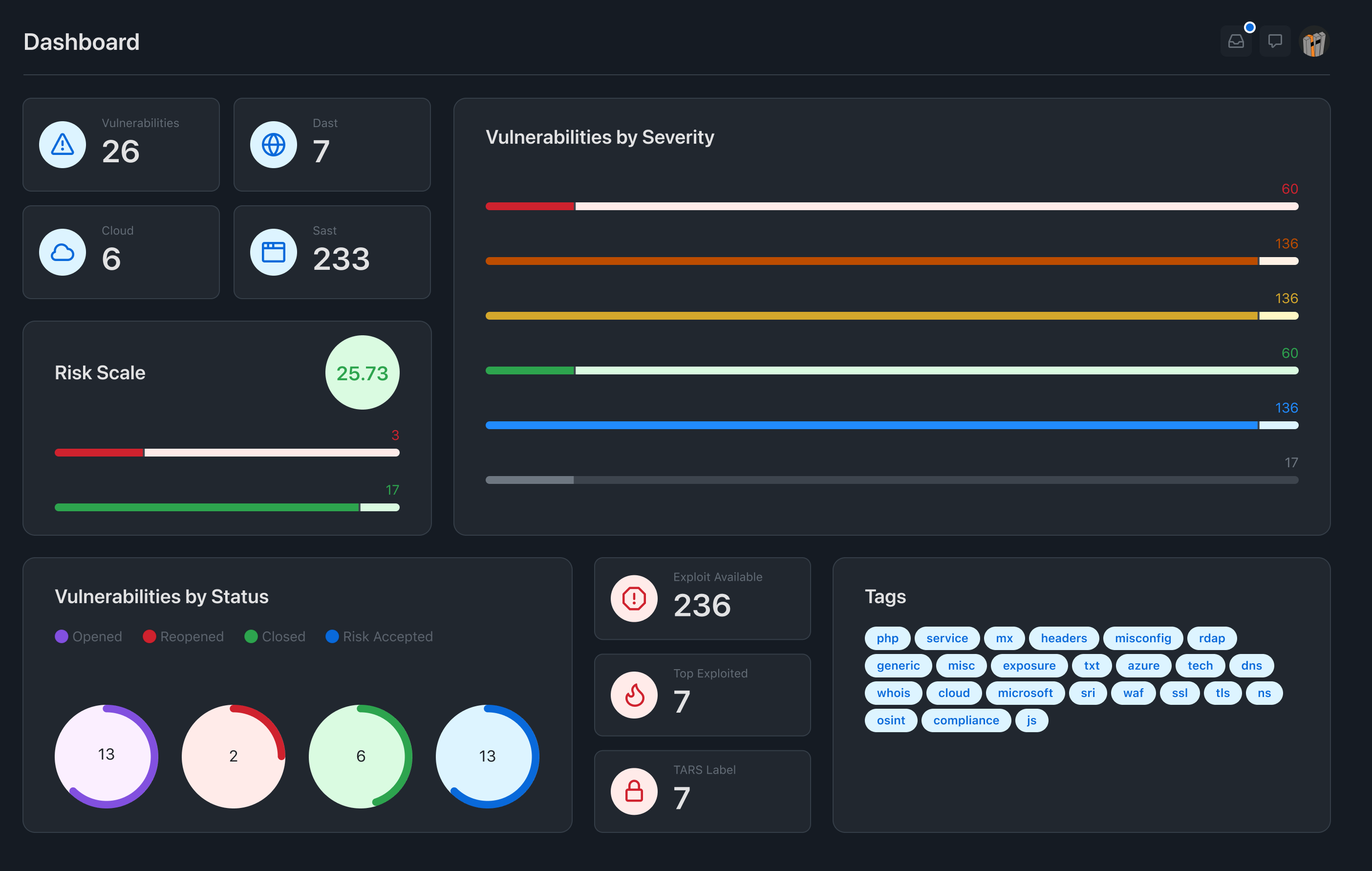
Vulnerability Management, SAST, DAST, SECRETS, SCA
Productivity
Code Security Instant vulnerability scanning and remediation without leaving your development environment
Process Automation Tars automates key security stages from scanning to reporting across build, test, and deployment pipelines.
Fast Scanning Automatic real-time vulnerability detection. Immediate identification of critical security issues requiring urgent attention.
CI/CD Integration Seamless integration with development and deployment workflows, detailed reports for control and audit.
Application Security
Empower Your Developers. Secure Code in Real-Time with Tars.
-
Tars Security CI/CD7m 34s
-
Sast0m 50s
-
Dast4m 14s
-
Secrets0m 56s
-
Sca0m 34s
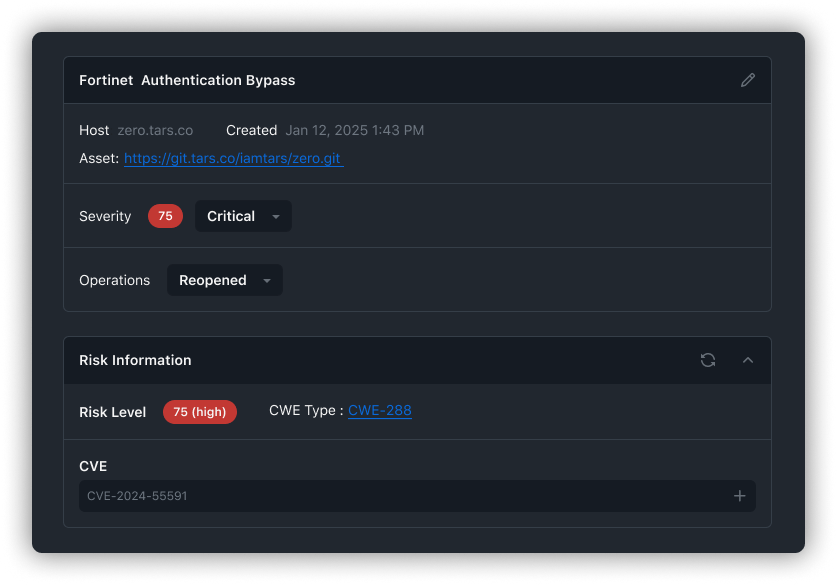
Find vulnerabilities
in your code using
static analysis. Prevent new vulnerabilities from being
introduced by scanning every pull request.
Supported Languages
Java, JavaScript,
TypeScript, Go, Rust, Python, Scala, C#, C, C++, Ruby,
PHP, Kotlin, Swift and others.
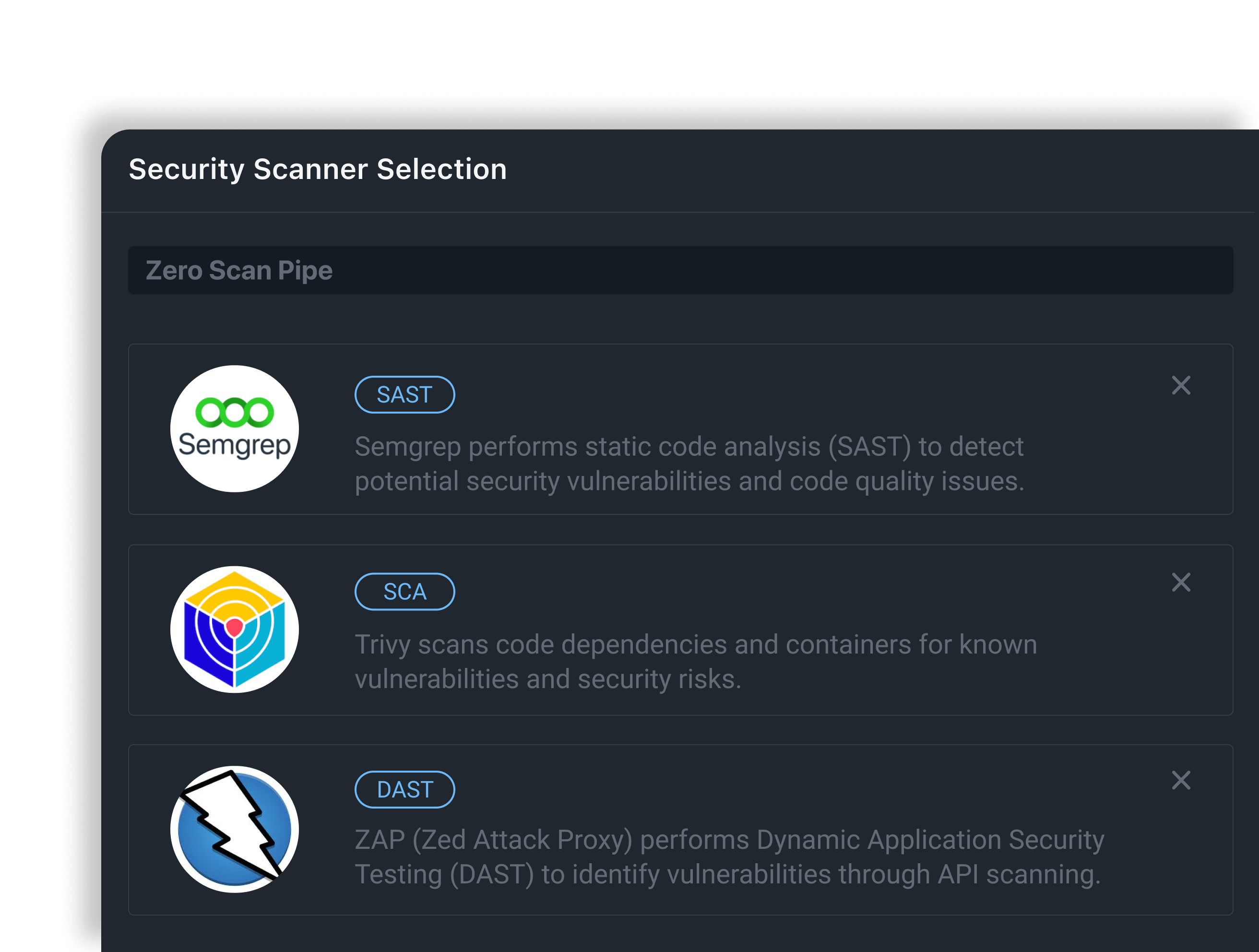
200+ Integrated Scanners
Unified
platform for all security tools: open-source
solutions, cloud services, and enterprise products
Optimization
Enhance Developer Experience. Shield your code in real-time with Tars. Empower your developers to build secure applications faster.
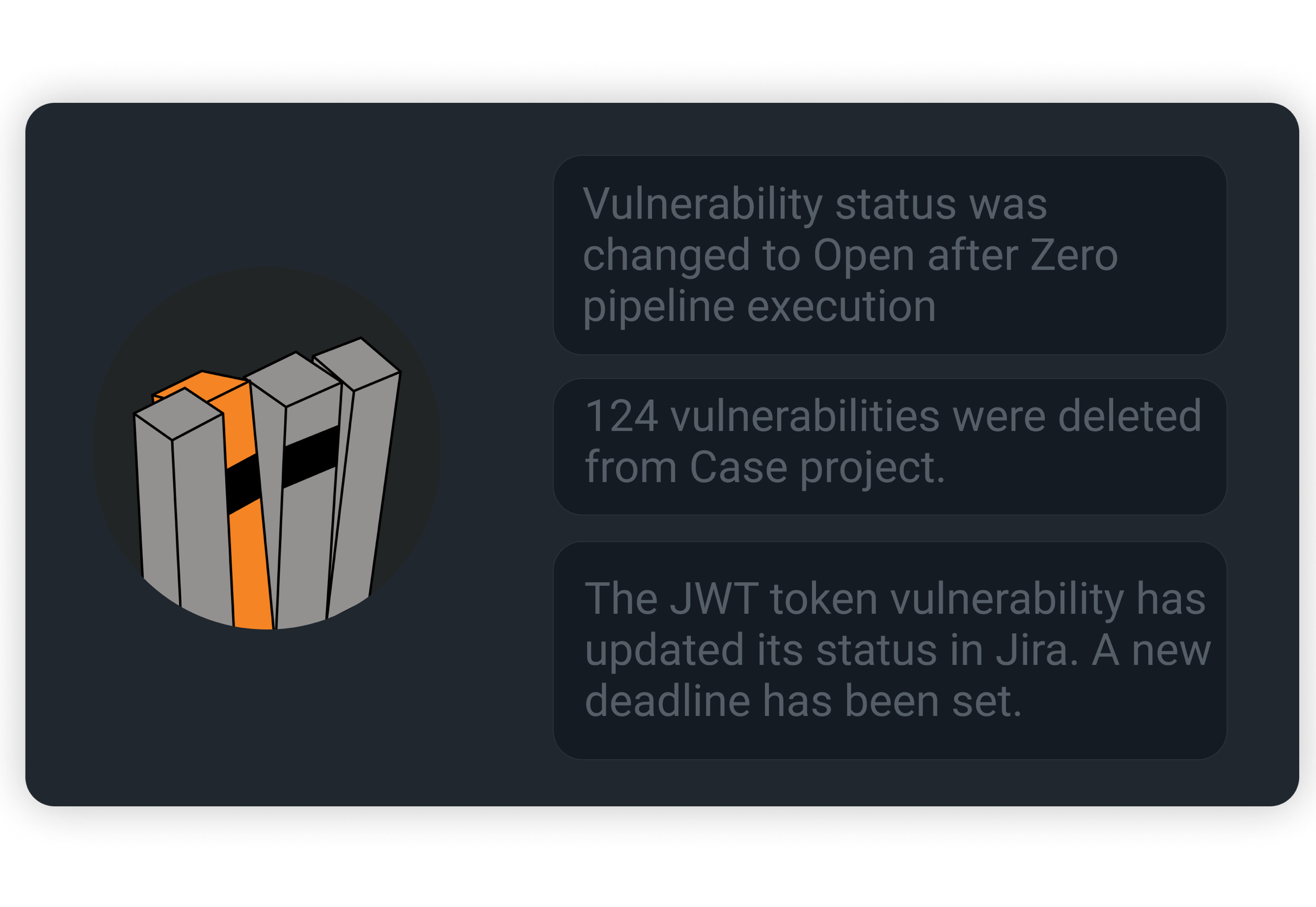
Centralized Control
Single source of truth for all vulnerability data with
comprehensive visibility and management through one
unified interface. Track and secure your project from
a central dashboard.
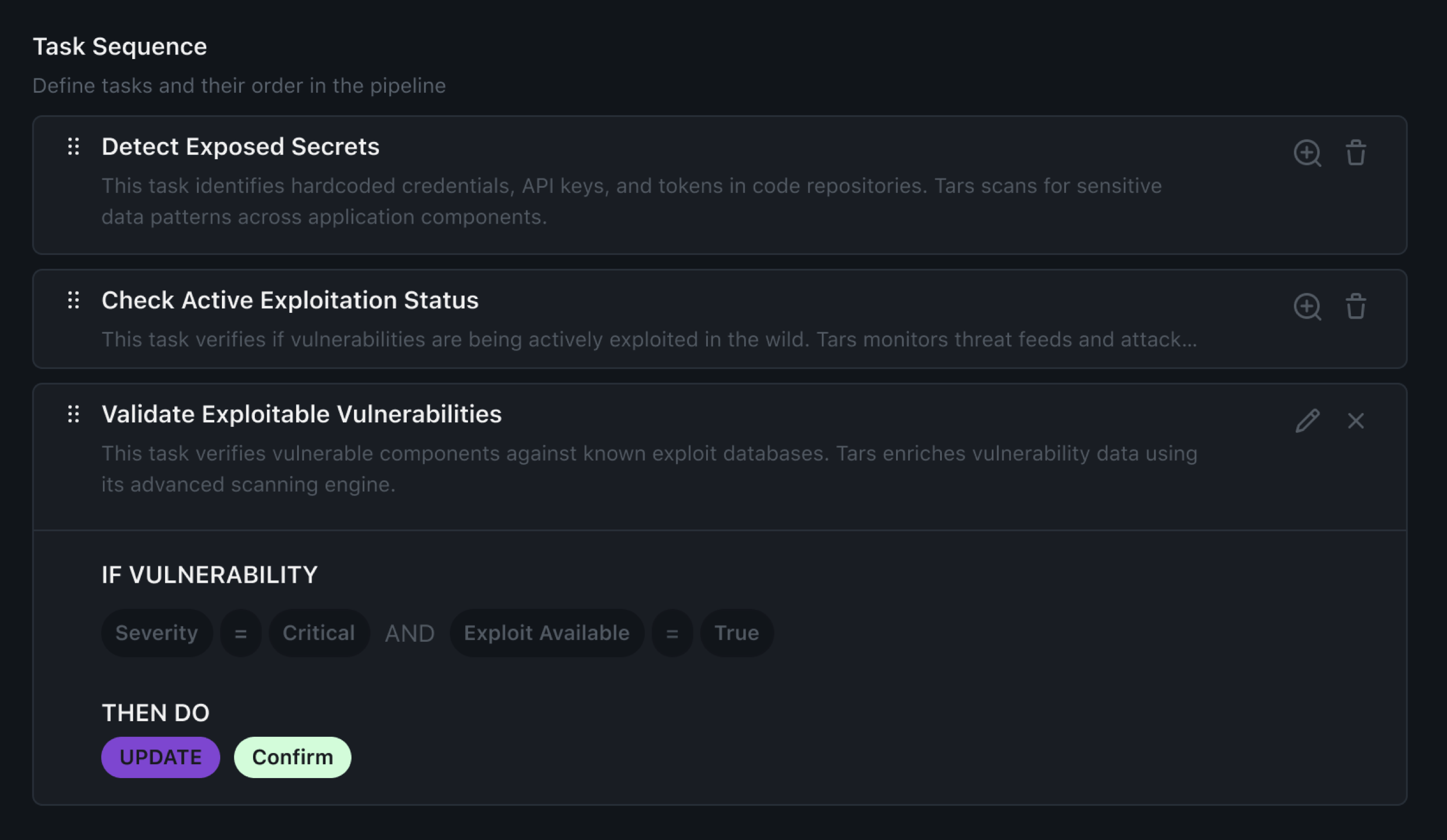
Flexible Workflows
Custom approval processes and automated task routing
based on priorities and team expertise. Optimize your
security operations with adaptable workflows.
Team Collaboration Streamline your workflow with integrated collaboration tools that enable quick task assignment, progress tracking, and seamless information sharing across your team.
Built-in AI
Tars leverages AI to analyze code, validate
vulnerabilities, and provide actionable fixes. Smart
recommendations accelerate remediation while
upskilling your team.
Pricing
Scale your protection. Tars for teams of any size
★ Recommended